适用于内部暂存区的 Azure Private Endpoint¶
This topic provides concepts as well as detailed instructions for connecting to Snowflake internal stages through Microsoft Azure Private Endpoints.
概述¶
Azure private endpoints (https://docs.microsoft.com/en-us/azure/private-link/private-endpoint-overview) and Azure Private Link (https://docs.microsoft.com/en-us/azure/private-link/private-link-overview) can be combined to provide secure connectivity to Snowflake internal stages. This setup ensures that data loading and data unloading operations to Snowflake internal stages use the Azure internal network and do not take place over the public internet.
Before Microsoft supported private endpoints for internal stage access, it was necessary to create a proxy farm within the Azure VNet to facilitate secure access to Snowflake internal stages. With the added support of private endpoints for Snowflake internal stages, users and client applications can now access Snowflake internal stages over the private Azure network. The following diagram summarizes this new support:
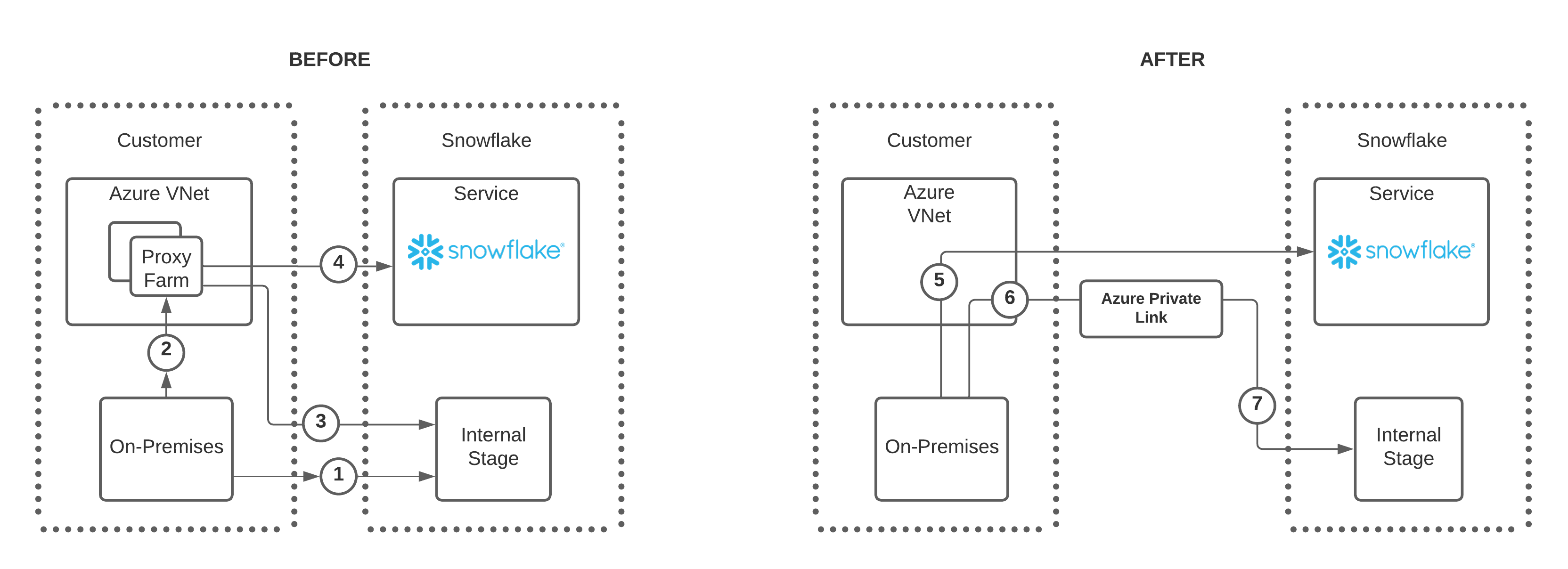
请注意以下有关 BEFORE 图中数字的说明:
用户可通过两种方式连接到 Snowflake 内部暂存区:
选项 A 可通过本地连接直接连接到内部暂存区,如数字 1 所示。
选项 B 可通过代理场连接到内部暂存区,如数字 2 和 3 所示。
如果使用代理场,用户还可以直接连接到 Snowflake,如数字 4 所示。
请注意以下有关 AFTER 图中数字的说明:
For clarity, the diagram shows a single private endpoint from one Azure VNet pointing to a single Snowflake internal stage (6 and 7).
Note that it is possible to configure multiple private endpoints, each within a different VNet, that point to the same Snowflake internal stage.
此功能更新后,无需通过代理场即可连接到 Snowflake 或 Snowflake 内部暂存区。
本地用户可以直接连接到 Snowflake,如数字 5 所示。
To connect to a Snowflake internal stage, on-premises user connects to a private endpoint, number 6, and then uses Azure Private Link to connect to the Snowflake internal stage as shown in number 7.
In Azure, each Snowflake account has a dedicated storage account to use as an internal stage. The storage account URIs are different
depending on whether the connection to the storage account uses private connectivity (that is, Azure Private Link). The private connectivity
URL includes a privatelink segment in the URL.
- 公共存储账户 URI:
<storage_account_name>.blob.core.windows.net- 专用连接存储账户 URI:
<storage_account_name>.privatelink.blob.core.windows.net
为您账户的内部暂存区:ref:配置 Azure Private Endpoint 连接<label-private_internal_stages_azure_configure_endpoints>`后,Microsoft Azure 会自动在公共 DNS 服务中创建一条 CNAME 记录,该服务将存储账户主机指向其 Azure 专用链接对应项。此对应项是 `.privatelink.blob.core.windows.net``。
优势¶
Implementing private endpoints to access Snowflake internal stages provides the following advantages:
Internal stage data does not traverse the public internet.
在 Azure VNet 外部运行的客户端和 SaaS 应用程序(如 Microsoft PowerBI)可以安全地连接到 Snowflake。
管理员无需修改防火墙设置即可访问内部暂存区数据。
管理员可以对用户连接到存储账户的方式实施一致的安全性和监控。
限制¶
Microsoft Azure defines how a private endpoint can interact with Snowflake:
A single private endpoint can communicate to a single Snowflake Service Endpoint. You can have multiple one-to-one configurations that connect to the same Snowflake internal stage.
您的存储账户中可以连接到 Snowflake 内部暂存区的 Azure Private Endpoint 的最大数量是固定的。有关详细信息,请参阅 标准存储账户限制 (https://learn.microsoft.com/en-us/azure/azure-resource-manager/management/azure-subscription-service-limits#standard-storage-account-limits)。
配置 Azure Private Endpoint 以访问 Snowflake 内部暂存区¶
To configure private endpoints to access Snowflake internal stages, you must have support from the following three roles in your organization:
The Snowflake account administrator (that is, a user with the Snowflake ACCOUNTADMIN system role).
Microsoft Azure 管理员。
网络管理员。
根据组织的不同,可能需要与多个人员或团队协调配置工作,以实施以下配置步骤。
Complete the following steps to configure and implement secure access to Snowflake internal stages through Azure private endpoints:
验证 Azure 订阅是否已注册到 Azure 存储资源管理器。此步骤允许您从专用端点连接到内部暂存区。
As a Snowflake account administrator, run the following commands in your Snowflake account and record the
ResourceIDof the internal stage storage account defined by theprivatelink_internal_stagekey. For more information, see ENABLE_INTERNAL_STAGES_PRIVATELINK and SYSTEM$GET_PRIVATELINK_CONFIG.USE ROLE ACCOUNTADMIN; ALTER ACCOUNT SET ENABLE_INTERNAL_STAGES_PRIVATELINK = true; SELECT KEY, VALUE FROM TABLE(flatten(input=>parse_json(system$get_privatelink_config())));
As the Azure administrator, create a private endpoint through the Azure portal.
View the private endpoint properties and record the resource ID value. You will provide this value as the
privateEndpointResourceIDfunction argument in the next step.验证该 Target sub-resource 值是否设置为
blob。有关更多信息,请参阅 Microsoft Azure 专用链接 文档 (https://docs.microsoft.com/en-us/azure/private-link/)。
重要
Before you proceed with the next step to authorize the private endpoint, you should be aware of the Microsoft Azure DNS behavior when a private endpoint is authorized on a storage location for the very first time.
When the first private endpoint is connected and authorized, Azure automatically creates a CNAME record in its public DNS for
storage-account-name.privatelink.blob.core.windows.net.Under normal circumstances, this DNS update should not affect existing public connectivity to the storage account. However, if your environment already has private DNS zones configured for
.privatelink.blob.core.windows.net, this DNS update can lead to unintended behavior. Specifically, existing storage clients attempting to access the public endpointstorage-account-name.blob.core.windows.netmay fail DNS resolution or be unable to reach the storage account using public IP.To avoid this issue, Microsoft recommends enabling the Fallback to Internet option in the private DNS zone configuration before authorizing the first private endpoint. This guidance also appears as a cautionary note in the Microsoft Azure DNS zone configuration documentation (https://learn.microsoft.com/en-us/azure/private-link/private-endpoint-dns#azure-services-dns-zone-configuration).
As the Snowflake administrator, call the SYSTEM$AUTHORIZE_STAGE_PRIVATELINK_ACCESS function using the
privateEndpointResourceIDvalue as the function argument. This step authorizes access to the Snowflake internal stage through the private endpoint.USE ROLE ACCOUNTADMIN; SELECT SYSTEM$AUTHORIZE_STAGE_PRIVATELINK_ACCESS('<privateEndpointResourceID>');
如有必要,请完成以下步骤以 撤消 对内部暂存区的访问权限。
让网络管理员参与更新专用 DNS 区域中的 DNS 设置。这些设置必须将专用链接 Blob URL
<storage_account_name>.privatelink.blob.core.windows.net解析到解析到连接您存储账户内部暂存区的 Azure Private Endpoint 的专用 IP 地址。有关更多信息,请参阅 Azure Private Endpoint DNS 配置 (https://docs.microsoft.com/en-us/azure/private-link/private-endpoint-dns)。
小技巧
使用单独的 Snowflake 账户进行测试,并在测试 VNet 中配置专用 DNS 区域以测试功能,这样一来,测试是隔离的,且不会影响其他工作负载。
如果无法使用单独的 Snowflake 账户,请使用测试用户通过已更改 DNS 的测试 VPC 访问 Snowflake。
To test from on-premises applications, use DNS forwarding to forward requests to the Azure private DNS in the VNet where the DNS settings are made. Run the following command from the client machine to verify that the IP address returned is the private IP address for the storage account:
dig <storage_account_name>.blob.core.windows.net
阻止公共访问 – 建议¶
After you configure private endpoints to access the internal stage using Azure Private Link, you can optionally block requests from public IP addresses to the internal stage. After blocking public access, all traffic must be through the private endpoint.
Controlling public access to an Azure internal stage differs from controlling public access to the Snowflake service. You use the SYSTEM$BLOCK_INTERNAL_STAGES_PUBLIC_ACCESS function, not a network policy, to block requests to the internal stage. Unlike network policies, this function can't block some public IP addresses while allowing others. Calling the SYSTEM$BLOCK_INTERNAL_STAGES_PUBLIC_ACCESS function blocks all public IP addresses.
重要
Confirm that traffic using private connectivity is successfully reaching the internal stage before blocking public access. Blocking public access without configuring private connectivity can cause unintended disruptions, including interference with managed services like Azure Data Factory.
The SYSTEM$BLOCK_INTERNAL_STAGES_PUBLIC_ACCESS function enforces its restrictions by altering the Networking settings of the Azure storage account where the internal stage is located. These Azure settings are commonly referred to as the "storage account firewall settings". Calling this Snowflake system function does the following actions in Azure:
将 Public network access 字段设置为 Enabled from selected virtual networks and IP addresses。
将 Snowflake VNet 子网 ID 添加到 Virtual Networks 部分。
从 Firewall 部分清除所有 IP 地址。
To block all traffic from public IP addresses to the internal stage, call the following function:
SELECT SYSTEM$BLOCK_INTERNAL_STAGES_PUBLIC_ACCESS();
The function can take a few minutes to complete.
确保阻止公共访问¶
To determine whether public IP addresses are able to access an internal stage, call the SYSTEM$INTERNAL_STAGES_PUBLIC_ACCESS_STATUS function.
If the Azure settings are currently blocking all public traffic, the function returns Public Access to internal stages is blocked.
This verifies that the settings have not been changed since the SYSTEM$BLOCK_INTERNAL_STAGES_PUBLIC_ACCESS function was called.
如果至少有一些公共 IP 地址可以访问内部暂存区,则该函数将返回 Public Access to internal stages is unblocked。
Unblocking public access¶
To allow public access to an internal stage that was previously blocked, call the SYSTEM$UNBLOCK_INTERNAL_STAGES_PUBLIC_ACCESS function.
Calling this function alters the Networking settings of the Azure storage account where the internal stage is located. It sets the Azure Public network access field to Enabled from all networks.
Revoking private endpoints to access Snowflake internal stages¶
To revoke access to Snowflake internal stages through Microsoft Azure private endpoints, complete the following steps:
作为 Snowflake 管理员,请确认 ENABLE_INTERNAL_STAGES_PRIVATELINK 参数已设置为
TRUE。例如:USE ROLE ACCOUNTADMIN; SHOW PARAMETERS LIKE 'enable_internal_stages_privatelink' IN ACCOUNT;
作为 Snowflake 管理员,调用 SYSTEM$REVOKE_STAGE_PRIVATELINK_ACCESS 函数以撤销对专用端点的访问权限,并使用最初用于授权访问该专用端点的相同
privateEndpointResourceID值。USE ROLE ACCOUNTADMIN; SELECT SYSTEM$REVOKE_STAGE_PRIVATELINK_ACCESS('<privateEndpointResourceID>');
作为 Azure 管理员,请通过 Azure 门户删除专用端点。
作为网络管理员,删除用于解析存储账户 URLs 的 DNS 和别名记录。
此时,对专用端点的访问权限已撤销。调用 SYSTEM$GET_PRIVATELINK_CONFIG 函数的查询结果不应返回 privatelink_internal_stage 键及其值。
故障排除¶
Azure applications that access Snowflake stages over the public internet and also use a private DNS service to resolve service host names cannot access Snowflake stages if a private endpoint connection is established to the stage as described in this topic.
If any application has configured a private DNS region for the same domain, then Microsoft Azure tries to resolve the storage account host by querying the private DNS service. If the entry for the storage account is not found in the private DNS service, a connection error occurs.
要解决此问题,请使用以下两个选项之一:
从应用程序移除专用 DNS 区域或取消其与应用程序的关联。
Create a CNAME record for the storage account private hostname --- that is,
<storage_account_name>.privatelink.blob.core.windows.net--- in the private DNS service and point it to the hostname specified by the output of this command:dig CNAME <storage_account_name>.privatelink.blob.core.windows.net